Encryption is like a big, impenetrable pipe…
… at least, that’s what I have to keep telling people who just don’t grok encryption, and think it’s some magic pixie-dust that you just sprinkle on anything and it’s imbued with magical protection.
I was trying to explain this to some MMORPG folks, who think that just because the communication between the client and server are “encrypted” that they can’t be tampered with. They’re 100% wrong.
Enter fwagglePxE – a proof-of-concept piece of software hacked together over about three days of rage-filled coding, after the company that ran the game in question left a nasty server bug in their software, which essentially robbed me of about $300 worth of imaginary shit. That’s $300 real dollars by the way.
Anyway, the game in question? Basically it uses a heinous modified version of AES-128 as a symmetric key cipher. The server sends IVs for the the encryption at the start of the session, and then the client and server just stay in sync with the algorithm and everything’s good. Indeed if you don’t stay in sync, then the encryption works just fine.
The problem is, if you catch the beginning of the session all the way through until the part you want, the encryption fails horribly. fwagglePxE worked by sitting on my router, which intercepted the connection and handed it to my software. My software then connected out to the game server, and then maintained two encryption states – one for the client and one for the server. If I so desired, I could even use different IVs for the client!
I borrowed most of the crypto stuff from a private server group, I just modified it a tiny bit to make it work the way I needed it (as a client as well as a server). From there it was a simple matter of writing an ncurses interface that included hexadecimal printouts of the plaintext packets, ANSI color printing to make things a little easier to understand, and a simple command parser that included the ability for me to enter hexadecimal strings, representing the bytes I wanted to inject.
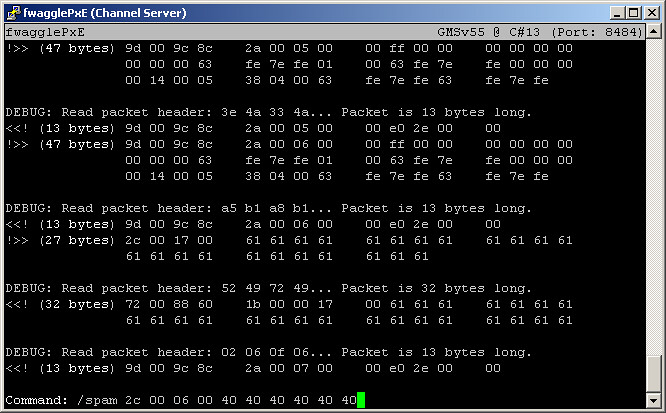
I eventually wound up writing parts into the editor that actually understood parts of the game logic, for example in the screenshot above you can see a couple of chat packets (spamming AAAAAAAA for example, and getting ready to spam six “@” characters)… I could do things like train it to ignore repeated messages from a single user that surpasses a certain threshold.
From the outside, it was probably the coolest thing I’d ever written. The feeling of elation I got when I got it to work was probably on-par with the feeling one gets when after hours of cracking, they finally get a “#” prompt on someone else’s machine. Technically it was the most advanced packet editor I knew of at the time, though a couple of people have written things that easily surpass my piece of shit. :( The code itself is terrible, a mish-mash of C++ written by someone who still thinks in C, and that’s why I never released it.
Anyway back to the rant at hand… imagine encryption as being a giant, impenetrable lead pipe. If the encryption is sound, at any point during the run of the pipe, there is absolutely no way you can see or tamper with things that are flowing inside the pipe.
However, if you can get to the ends of the pipe, there’s no reason you can’t take a peek there. That’s the thing most people don’t understand about encryption, is if you can control either end of the pipe then absolutely nothing can be guaranteed. “All bets are off” as many people like to say.
Which makes this entire rant more or less just a thinly veiled excuse to show off the only remaining evidence of my neato-elito packet editor. :(